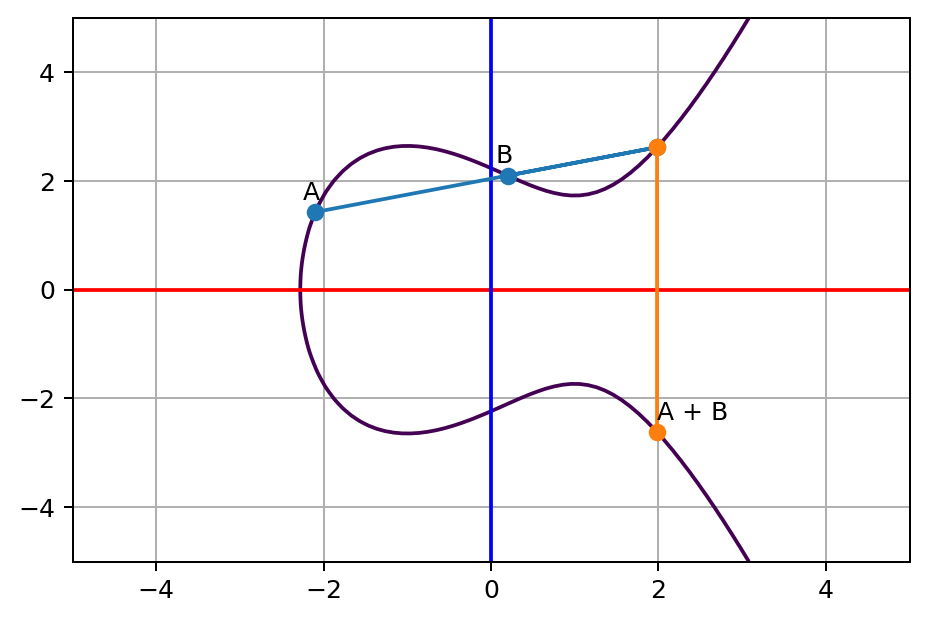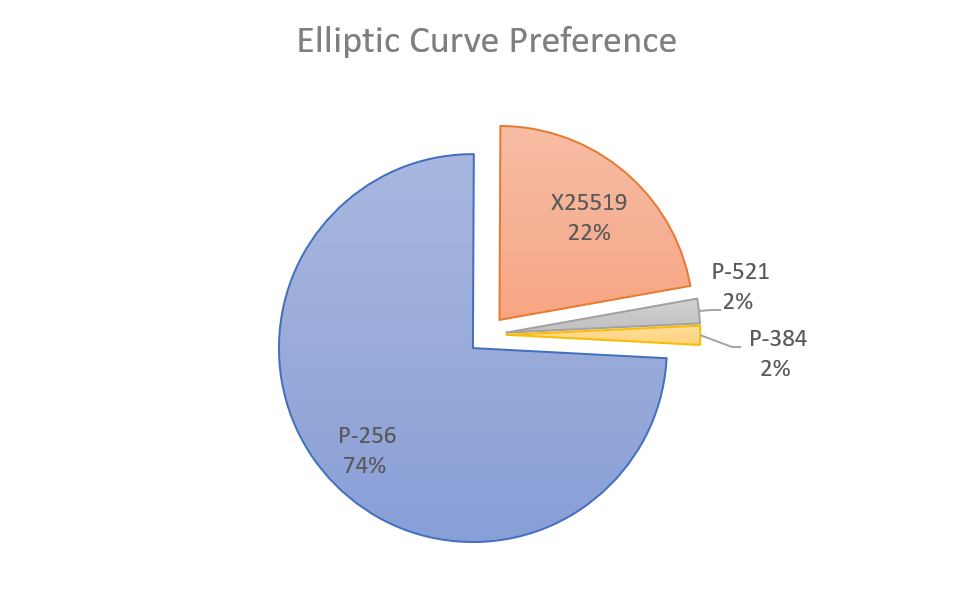
Everyone Loves Curves! But Which Elliptic Curve is the Most Popular? - Malware News - Malware Analysis, News and Indicators

EW_{256357}$$ : A New Secure NIST P-256 Compatible Elliptic Curve for VoIP Applications' Security | SpringerLink
A generalized framework for elliptic curves based PRNG and its utilization in image encryption | Scientific Reports
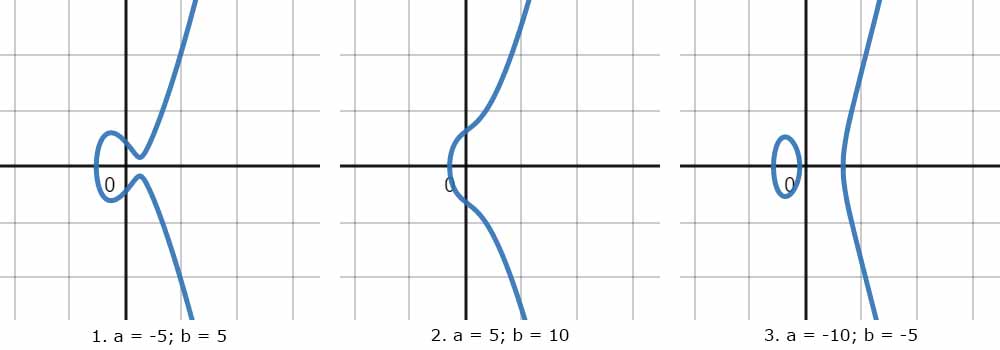
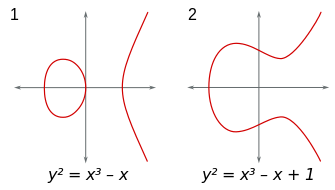
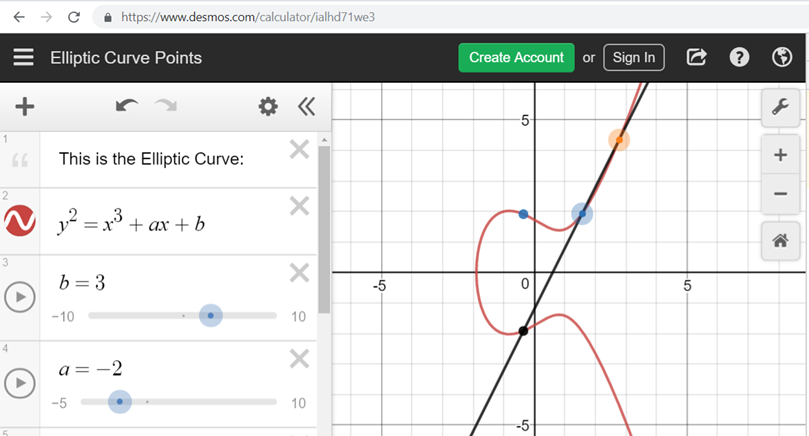
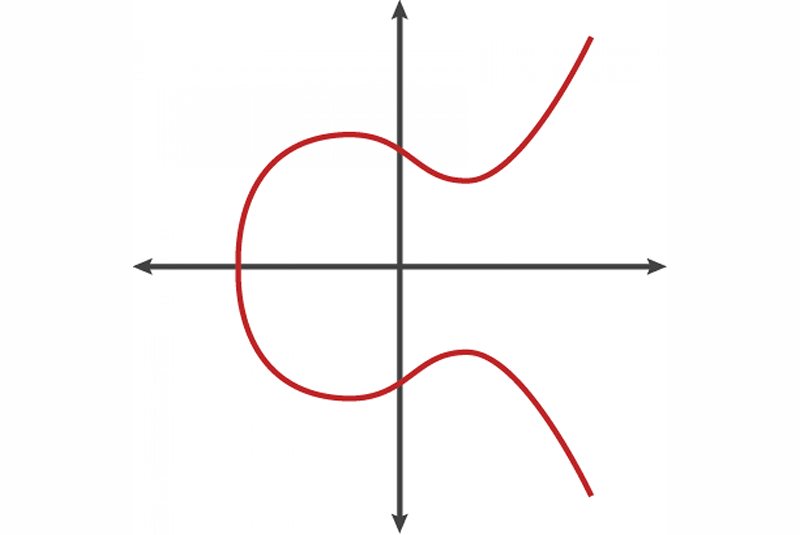
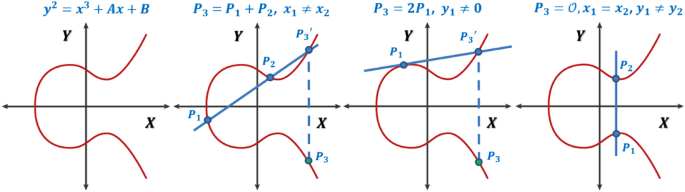
Mathematics of Elliptic Curve Cryptography (ECC) | Microsec.com - /en/pki-blog/mathematics-elliptic-curve-cryptography-ecc

Analysis of standard elliptic curves for the implementation of elliptic curve cryptography in resource-constrained E-commerce applications | Semantic Scholar

Table I from Analysis of standard elliptic curves for the implementation of elliptic curve cryptography in resource-constrained E-commerce applications | Semantic Scholar

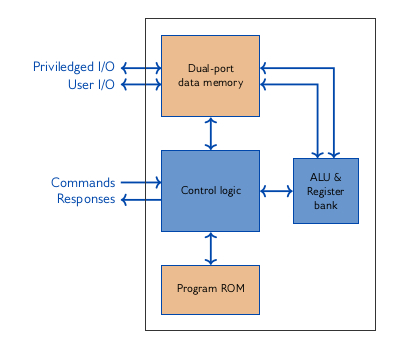
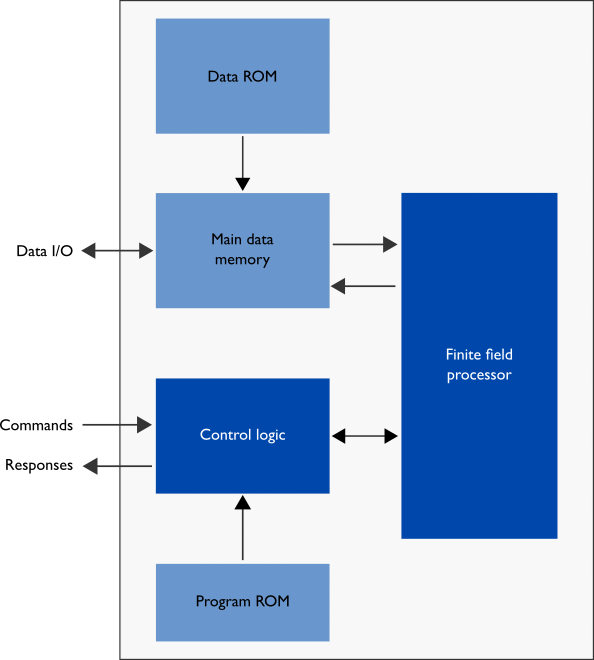
Implementing efficient 384-bit NIST Elliptic Curve over prime fields on an ARM946E | Semantic Scholar
Will all five NIST Elliptic Curves Seeds be cracked within 6 months of the bounty announcement? | Manifold

Everyone Loves Curves! But Which Elliptic Curve is the Most Popular? - Malware News - Malware Analysis, News and Indicators